Public GitHub repositories are increasingly leaking secrets
1 min read
GitGuardian have released their annual report of secrets exposed on public GitHub repositories. There are some depressing statistics revealed here.
- 12.8 million new secrets were leaked in 2023, a 28% increase from the previous year
- Over 1 in 10 commit authors contributed a leaked secret
- 90% of exposed secrets remained active 5 days after the leak, in other words credentials weren’t changed after the leak leaving a system exposed
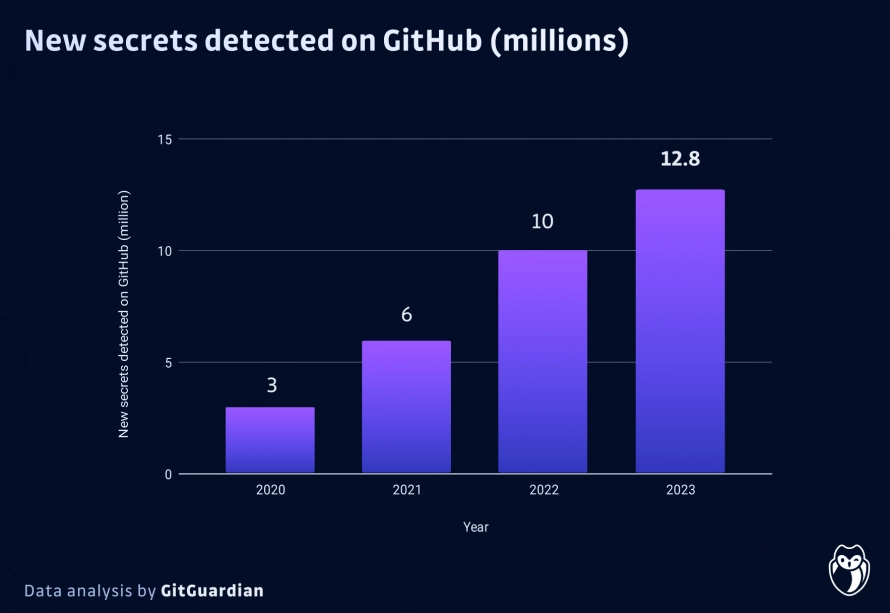
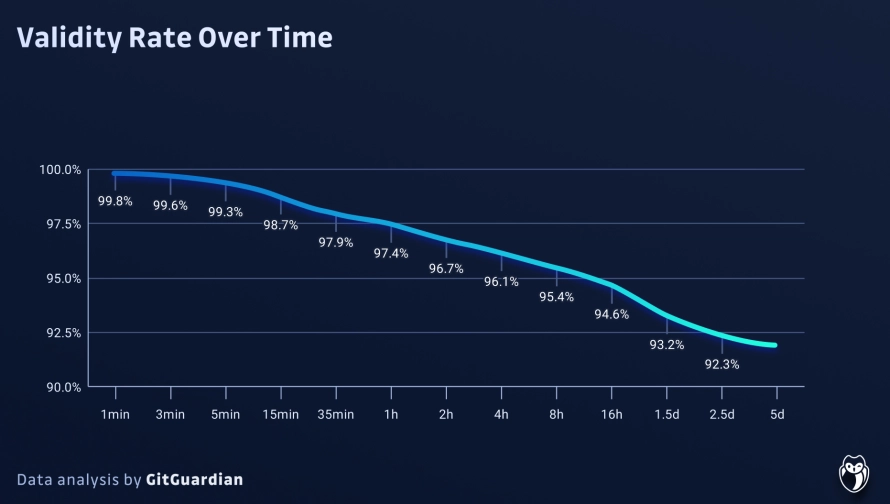
Sophos found that in 2023 compromised credentials took the top spot in root causes of attacks. As developers, we clearly need to be more conscious of what we are committing to repositories and aware of the risks.
I remember many years ago discovering a GitHub search query that was circulating the web at the time; it would return files containing certain login credentials. Many of these would work if you tested them. Sadly it seems lessons have not been learnt.